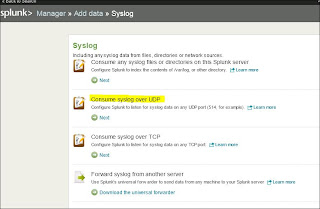
So the initial code is pretty simple. When you run the script it will dump to your Powershell console. But what if I don't want to review it just yet and save it for later? I could dump the results to a file with a number of methods, but I really want to make sure I check it out. So why not generate a web page with the results? That would be perfect!! Powershell has a number of ConverTo-X commands, they happen to have one for ConvertTo-HTML. Here is the modified code:
Invoke-RestMethod -Uri $sg2013 | select title, pubdate, link |
ConvertTo-Html | Out-File E:\Code\Powershell\rss_reader.html
Notice I also added the link to the select statement. The last half of the code sends the information to the designated out-file. But I am not fond of the results.
See? Very boring. Believe it or not, there is quite a bit of code present in the page. Since the Conversion occurs with the original output in a table format, it actually created it as such in the html. Unfortunately no color. Lets see if we can spruce things up a bit. With a bit more research into ConvertTo-Html, I found that it has options for the various sections of an HTML file: HEAD, BODY, and TITLE. For this example we will stick with working in the HEAD section. In the HEAD section we could call various STYLE configurations that will apply to the whole page. A new variable will need to be created that will contain the content for the HEAD section:
$style = "<style>BODY{background-color:black;}</style>"
Invoke-RestMethod -Uri $sg2013 | select title, pubdate, link |
ConvertTo-Html -head $style | Out-File E:\Code\Powershell\rss_reader.html
We are almost there, unfortunately this creates a page with a black background, not good since the font color is also black. The style variable can be further declared using a series of "$style = $style + ..." calls.
$style = "<style>"
$style = $style + "BODY{background-color:black;}"
$style = $style + "BODY{color:lime;}"
$style = $style + "</style>"
That is much better, you can experiment with the colors if black and lime green are not your thing. We will add one more option to the ConvertTo-Html function using the -body option:
Invoke-RestMethod -Uri $sg2013 | select title, pubdate, link |
ConvertTo-Html -head $style -body "<H2>2013 Scripting Games Feed</H2>" | Out-File E:\DMZ\Code\Powershell\rss_reader.html
This adds a nice heading to the page. So this is great, I have a nicely formatted list of items from the Scripting Guy's blog, but how do I remember to go back and check??? Well you can call the following command in the script to open the file in a browser:
Invoke-Expression E:\Code\Powershell\rss_reader.html
This will open the HTML file up in your default browser. So if you want to get really crazy, add this as a scheduled task to run every couple hours/days/weeks etc. A couple things I will be trying to add are some conditions so that I don't just keep getting a full list of items. I may only want to view the latest posts and I may want the list to convert the links to hyper-links. Well I hope you enjoyed, now go out and code!